Protecting your personal information online starts with understanding the language of the internet. We’ll break down five essential tech terms that directly affect your online privacy, from the secretive Dark Web to the nuances of email etiquette.
Learning these concepts will equip you to navigate the internet more securely.
Stay tuned for more in this series as we dive deeper into privacy-related tech terms and other essential concepts, answering the top questions we get from readers like you!
GET THE LATEST TECH TERMS, SECURITY ALERTS, TOP TECH TIPS, AND DIGITAL TRENDS STRAIGHT TO YOUR INBOX. SIGN UP FOR KURT’S CYBERGUY REPORT—IT’S FREE!
People working on their laptops (Kurt “CyberGuy” Knutsson)
The Dark Web
A hidden internet below the surface
Beneath the familiar internet you browse every day lies the Dark Web, a concealed layer of the internet that isn’t indexed by search engines like Google and requires specialized software, such as the Tor browser, to access.
Originally developed by the U.S. Navy in the 1990s for secure and anonymous communication, the Dark Web has since evolved into a double-edged sword, a haven for privacy advocates, journalists and whistleblowers, as well as a hot spot for cybercriminals engaging in illicit activities.
While some use the Dark Web for legitimate purposes, like bypassing censorship or protecting free speech, it’s also a marketplace for stolen personal data, financial fraud and illegal goods, making it a high-risk zone for identity theft.
If you want to safeguard your personal information from being bought, sold or leaked on the Dark Web, consider using identity monitoring services that scan underground forums and databases for exposed data.
If you want to make sure your data stays out of nefarious hands and away from the Dark Web, consider identity monitoring services that can scour the internet for your data and remove it for you.

Illustration of a hacker on the Dark Web (Kurt “CyberGuy” Knutsson)
BEST ANTIVIRUS FOR MAC, PC, IPHONES AND ANDROIDS – CYBERGUY PICKS
Encryption
Securing your digital world, one byte at a time
Ever wonder how your online banking info stays safe? That’s thanks to encryption, a process that scrambles your data into a secret code so only authorized people (or devices) can read it.
How encryption works:
- Turns data into unreadable text – If intercepted, it looks like gibberish.
- Only the right system can unlock it – Your bank, email provider or messaging app automatically decrypts it so you see normal text.
Where you use encryption every day:
- Secure websites – Look for HTTPS (the “S” means encrypted).
- Messaging apps – WhatsApp and iMessage use end-to-end encryption.
- Online banking and shopping – Protects your financial transactions.
Encryption keeps prying eyes out and your private info safe because not everything you do online should be an open book. Check out other tips to protect your documents and keep them private.
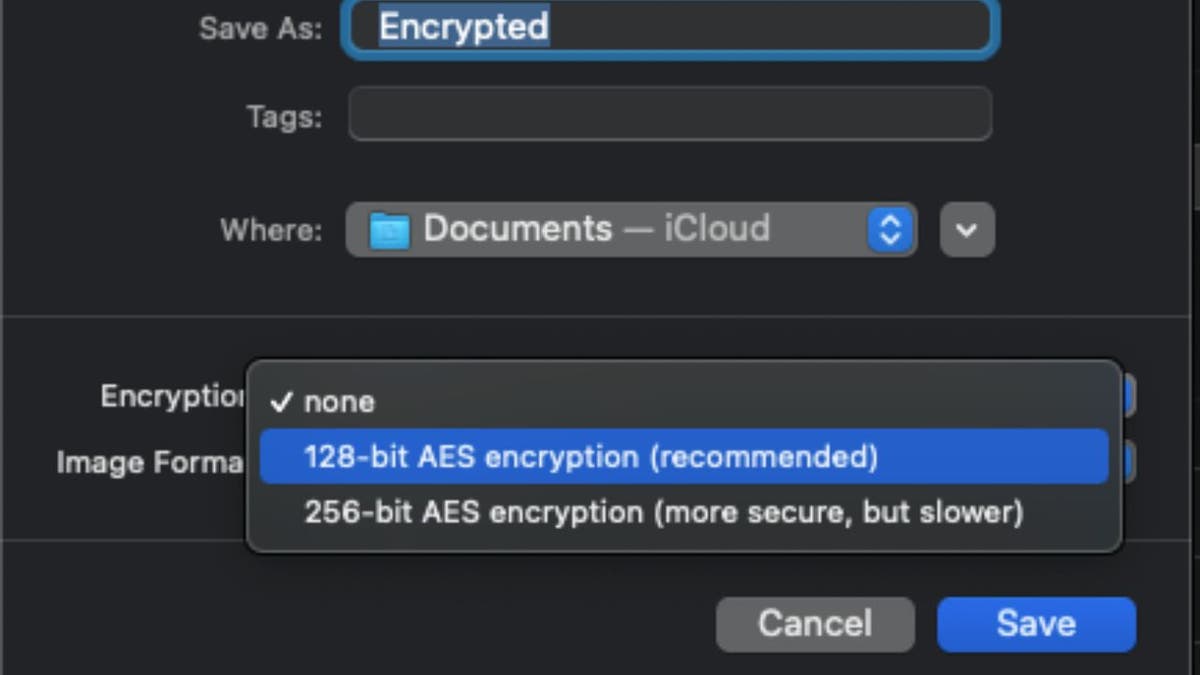
Saving a document with encryption (Kurt “CyberGuy” Knutsson)
BEST LAPTOPS OF 2025
CAPTCHA
Proving you’re human online
Have you ever had to click on pictures of traffic lights or type in wavy letters before logging onto a website? That’s a CAPTCHA, a simple test designed to tell humans and bots apart.
Websites use CAPTCHAs to block automated programs (like spambots) from accessing accounts, submitting fake forms or posting junk. The name stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.”
So what’s a Turing test? Named after computer scientist and WW2 codebreaker Alan Turing, it’s a challenge to see if a machine can act so much like a human that people can’t tell the difference. CAPTCHAs flip the idea around, making sure you’re human, not a bot!
While some CAPTCHAs ask you to solve puzzles, newer versions just check if your mouse movements look human. So next time you prove you’re “not a robot,” you’re actually helping protect the internet.
But not all CAPTCHAS are created equal. Follow my guide to learn how to spot the signs of a fake CAPTCHA designed to download malware.
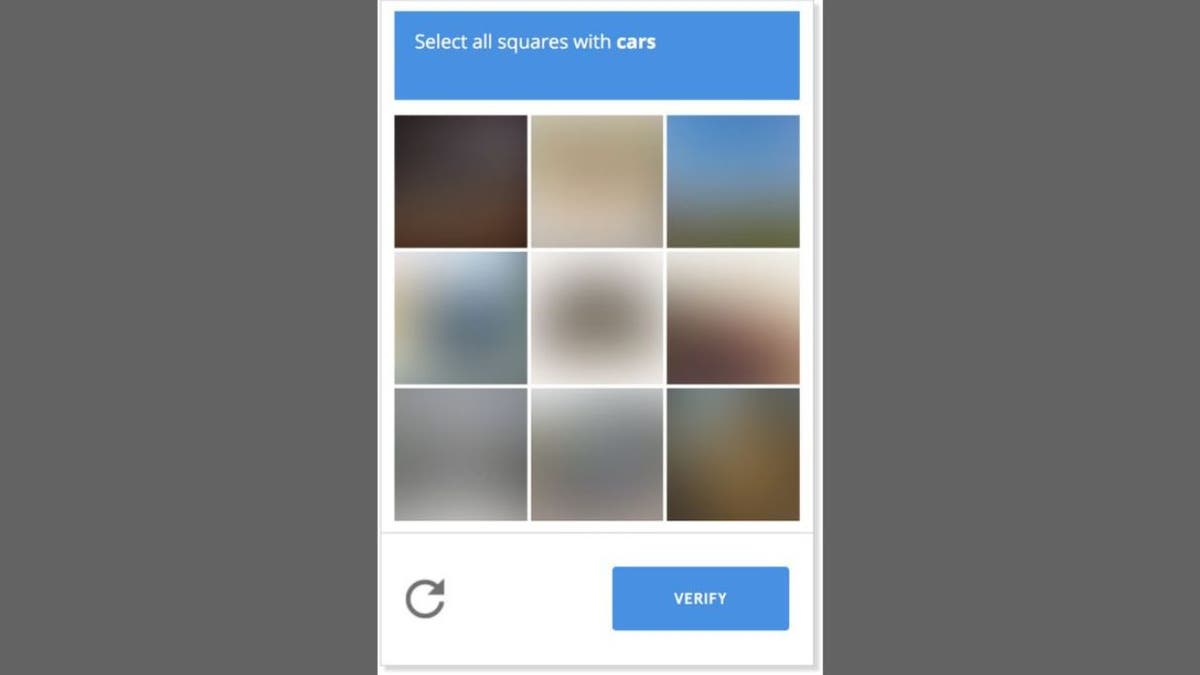
Website using Captcha (Kurt “CyberGuy” Knutsson)
BEST TECH FOR PERSONAL PROTECTION IN 2025
Spam
From Monty Python to malware: The evolution of spam
The term “spam” for unwanted email comes from a Monty Python sketch where the word “Spam” (referring to the canned meat) is repeatedly mentioned, overwhelming the conversation. This led to the term being used to describe the overwhelming nature of unwanted email: spam.
Originally, spam was just a nuisance flooding inboxes with promotional emails, chain letters and irrelevant ads. But, over time, spam has evolved into a major cybersecurity threat. Phishing emails, malware-laden attachments and fraudulent schemes now lurk within spam messages, tricking unsuspecting users into clicking malicious links, revealing sensitive information or even infecting their devices with ransomware and spyware.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?

A woman encountering spam on her laptop (Kurt “CyberGuy” Knutsson)
CC/BCC
Who sees what? Mastering email copies
Believe it or not, you may already know what the nicknames for these tech terms come from. If you’ve ever sent an email, you’ve probably seen CC and BCC. But what are they for?
CC stands for “carbon copy,” a throwback to the days of typewriters when carbon paper made duplicate copies. In email, it means sending a copy of your message to someone so they can stay informed. Everyone can see who’s been CC’d, making it great for keeping people in the loop without needing them to respond.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
BCC stands for “blind carbon copy.” It’s like CC but private. Recipients in the BCC field get the email, but their names and addresses aren’t visible to others. This is handy for group emails where you want to protect privacy or avoid a reply-all storm.
These tools help you manage communication and keep everyone on the same page. Looking to switch up your email provider to a more secure and private platform? Check out my picks – I’ll take you through the pros and cons.
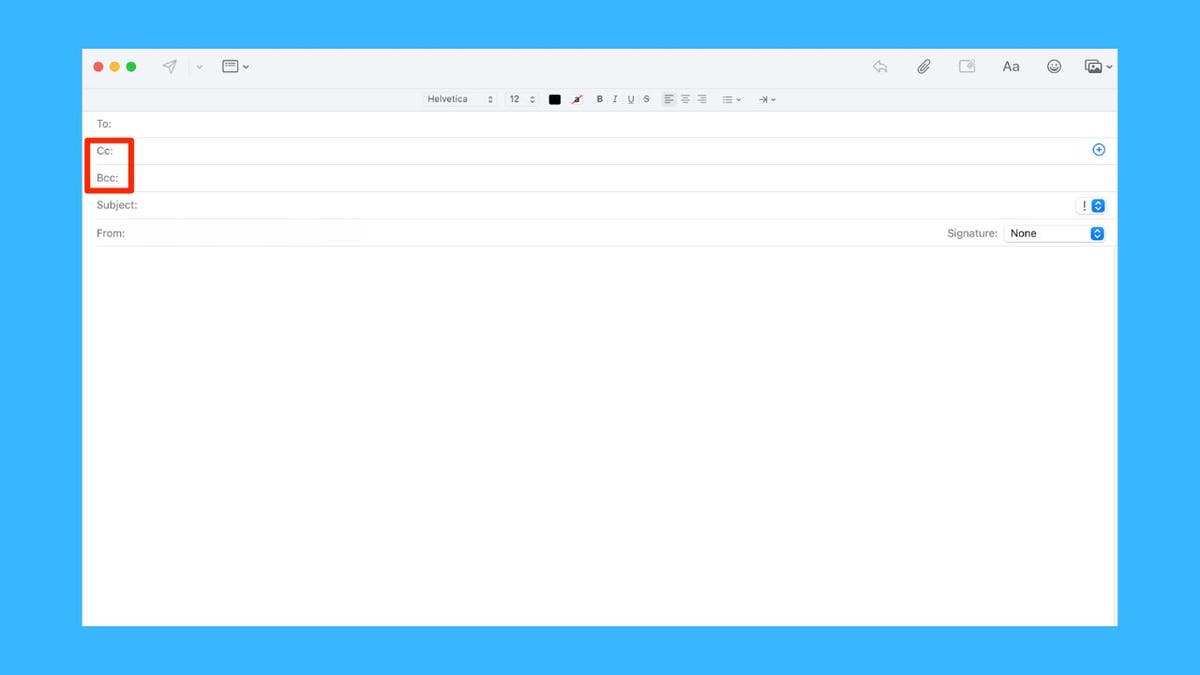
CC/BCC outlined in red (Kurt “CyberGuy” Knutsson)
Kurt’s key takeaways
Understanding these five privacy-related tech terms is essential. The Dark Web highlights the need to protect your personal data. Encryption is your digital shield, securing your information during online activities. CAPTCHAs help protect websites from automated attacks, which indirectly preserves your security. Recognizing spam protects you from phishing and malware. And using CC and BCC correctly in emails respects privacy. By knowing these concepts, you’re better equipped to enhance your online privacy and security.
CLICK HERE TO GET THE FOX NEWS APP
Confused by a tech term or want something explained? We want to hear from you! Share your questions at Cyberguy.com/Contact so we can help.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover
Follow Kurt on his social channels
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.